The Advanced Encryption Standard (AES), also known as Rijndael (AES author’s name), has been the standard level of encryption since 2001. Encryption works by a series of steps. User data is called plaintext, which is not encrypted. AES is applied to plaintext to transform plaintext into ciphertext, which is encrypted. The AES encryption process uses “keys” to transform data from plaintext to ciphertext, and from ciphertext to plaintext.
Key Schedule
AES uses a process called “key schedule” as their algorithm to determine which plaintext input character is transformed with a key to which ciphertext character. The application of the key schedule is called key expansion. Key expansion occurs in either 128-bit, 192-bit, or 256-bit. Each configuration is unique. There are ten transformation rounds for 128-bit keys, twelve transformation rounds for 192-bit keys, and fourteen transformation rounds for 256-bit keys. Each transformation rounds consists of several steps of various algebraic equations such as shifting two bits to the left or adding a round key using bitwise XOR.
Bitwise
Bitwise is a binary operation that takes two bit patterns (0’s and 1’s) of equal length and performs the logical exclusion “or” operation on each pair of corresponding bits (i.e., “00”, “01”, “11”, “10”). If one of the bits is 1, then the bitwise XOR result is 1; if both bits are 0 or 1, then the bitwise XOR result is 0. Remember, “0” means “off” and “1” means “on” at the granular level of computing.
There are rules that the AES process follows based on the number of characters in plaintext. Words with six characters follow different encryption rules than words with eight characters, for example.
Part of the AES algorithm includes conversion from text to binary. For example, capital “A” on the ASCII (American Standard Code for Information Interchange) table is represented by “01000001”. AES uses a key to manipulate the sequence of 0’s and 1’s. Each manipulation of the sequence is basically a transformation round.
How Secure is Encryption?
Idera states that an AES 128-bit encryption has never been cracked. Still, 256-bit is deemed more difficult to crack, and is the go-to encryption level when processors can handle the extra demands of 256-bit. A 256-bit encryption requires faster chip processing speeds than 128-bit encryption. AES uses a symmetric algorithm, using the same key for both encryption and decryption.
Proprietary Software vs OTS Software
Companies that use software can either design their own software (proprietary), or augment software from an industry expert by adding unique features to transform the expert software into a customized user experience. Companies that create proprietary software are ultimately responsible for the entire security of their software as well as the security of the data that users run through (or storage of data within) the proprietary software. Most companies do not have the same degree of encryption enabled on proprietary software that the biggest software experts guarantee, like Microsoft. Therefore, OTS (off-the-shelf) software is a popular choice.

The main reason to use an OTS software is money savings. OTS software providers are generally experts in the field, i.e., Microsoft. Microsoft’s market cap in May 2021 is $1.85 trillion. Microsoft likely spends billions of dollars on securing encryption of data. Much smaller companies that specialize in making user software experiences fit user’s needs opt for OTS software tenants, specifically to save money and pass those savings onto their clients.
Microsoft offers many OTS software solutions, i.e., Office 365, SharePoint, Dynamics. Microsoft OTS also offer AES encryption to all OTS products and is extended to the software companies that customize an OTS solution to a portfolio of clients that wish a more customized software. An example of this is Dock 365, which builds customized contract management software on the Microsoft SharePoint OTS. Dock 365 is a Microsoft Certified Gold Partner. Clients of Dock 365 are ensured enterprise security from Microsoft.
Microsoft Encryption
Microsoft OTS software offers encryption of data in transit and data at rest.
Data in Transit Encryption
Data in transit refers to data that is being transferred from one location to another. Data that starts with the user is encrypted with Secure Sockets Layer (SSL) encryption before moving to a datacenter and moving from one datacenter server to another.
Data at Rest Encryption
Data at rest refers to data that is not being transferred anywhere, such as document files stored in file folders on a local drive. Microsoft uses both disk encryption and file encryption.
Disk Encryption
Disk encryption is employed with BitLocker, which protects user metadata. BitLocker is a full volume encryption feature of Microsoft Windows versions starting with the Vista generation. BitLocker is a logical volume encryption system. A volume spans part of a hard disk drive, the whole drive or more than one drive.
During disk encryption, partial data removed from the datacenter is unreadable without the remainder of the data. All data is stored in parts. For example, A, B, C, D. For data to be readable, the correct encryption code must be used on each unique part. If “B” is moved to a new datacenter or compromised, it will remain unreadable unless parts “A”, “C”, and “D” are moved with part “B”, and if all encryption codes are compromised. The likelihood of all parts being decrypted successfully outside of the Microsoft environment is extremely rare.
File Encryption
File encryption occurs by data reassembly from English, for example, to AES 256 code (256-bit keys) and is compliant with Federal Information Processing Standard (FIPS). To access, or read, the AES code, a unique key must be used. Just like with disk encryption, Microsoft saves files that are larger than 64 kb in parts, like the “A”, “B”, “C”, “D” example in the previous paragraph. Each part has its own encryption key. Software updates include encryption as well. File “parts” are stored in separate Microsoft Azure storage containers, randomly, to further protect user data. The encryption keys to each part are locked in Microsoft Key Store. Keys are stored in the Microsoft Content Database. The keys are encrypted also. So, first the data is encrypted. Then, data is stored in parts. Each part has a unique key that is also encrypted.
encryption, Microsoft saves files that are larger than 64 kb in parts, like the “A”, “B”, “C”, “D” example in the previous paragraph. Each part has its own encryption key. Software updates include encryption as well. File “parts” are stored in separate Microsoft Azure storage containers, randomly, to further protect user data. The encryption keys to each part are locked in Microsoft Key Store. Keys are stored in the Microsoft Content Database. The keys are encrypted also. So, first the data is encrypted. Then, data is stored in parts. Each part has a unique key that is also encrypted.
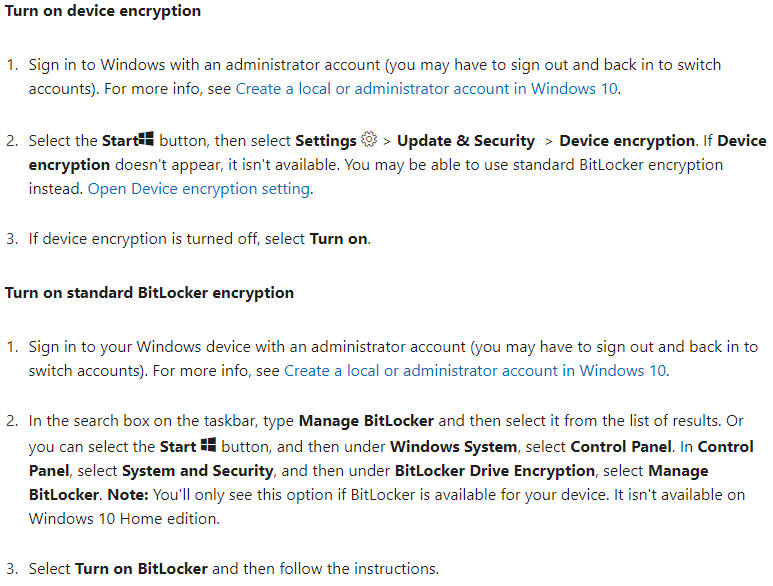
BitLocker Settings
Users can turn on BitLocker encryption from the “Start” button. View instructions from Microsoft here and see the steps below.
Summary
Data encryption is most secure when employing AES standards. Make sure that all proprietary and private data is encrypted with AES standards. Individual users can ensure AES standards by using software built by Microsoft or an equivalent expert in software programming, or by using customized software built on an OTS Microsoft tenant, such as SharePoint, Dynamics, Office 365.
Book a Live demo
Schedule a live demo of Dock 365's Contract Management Software now.







